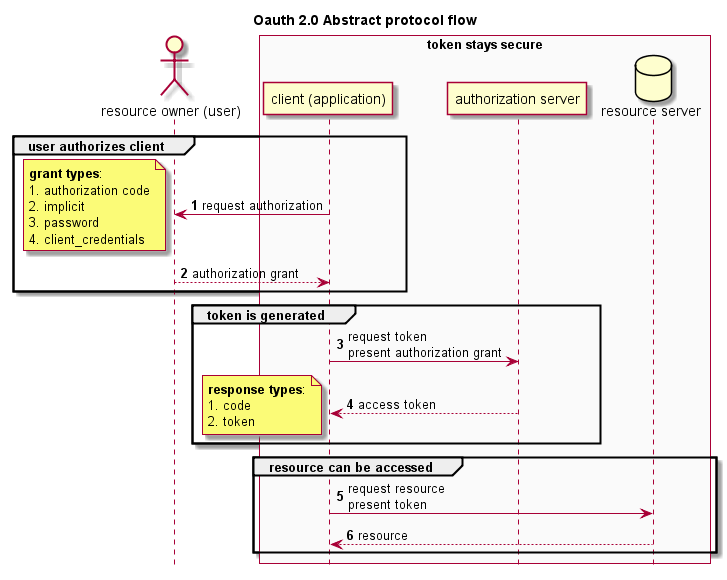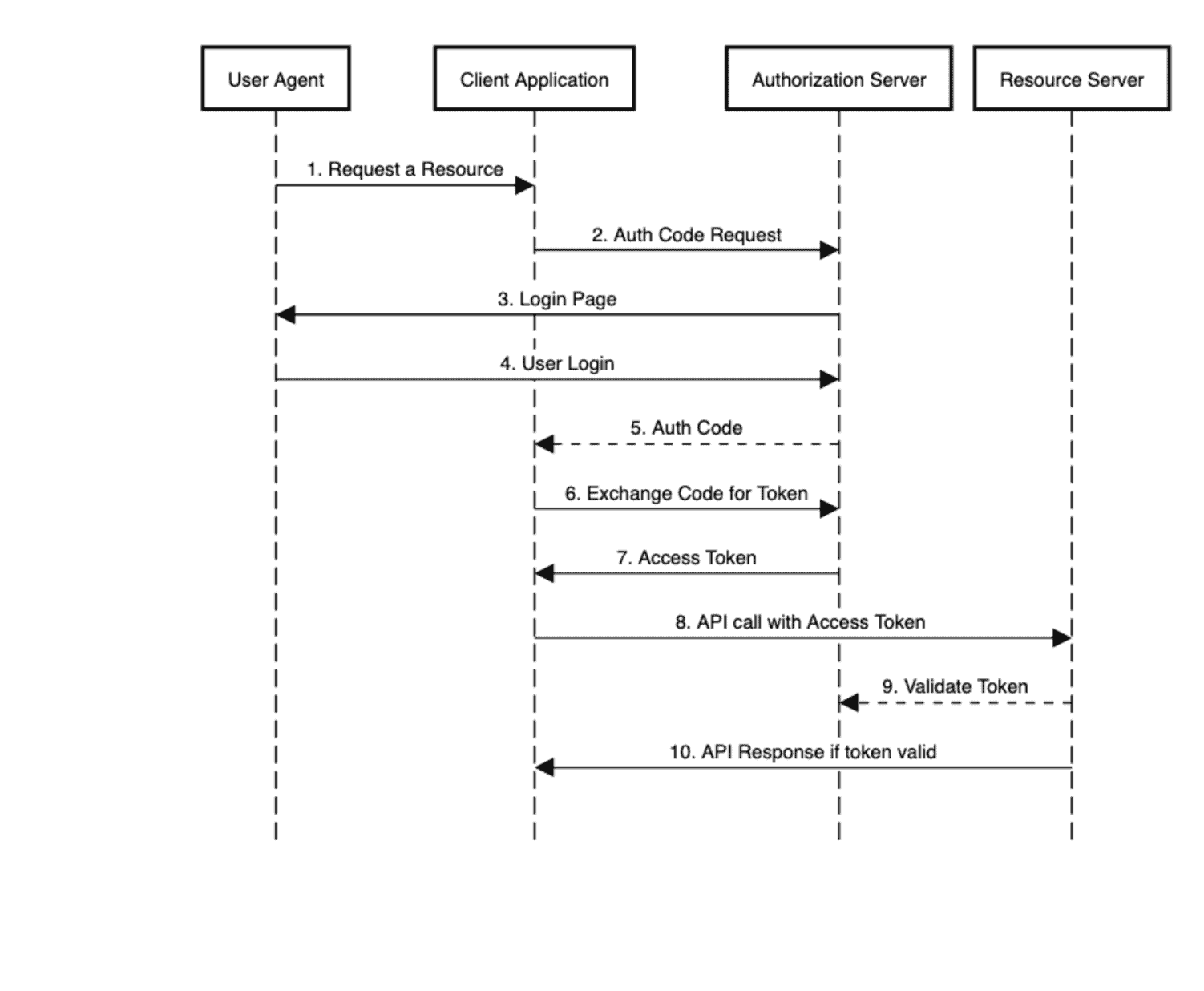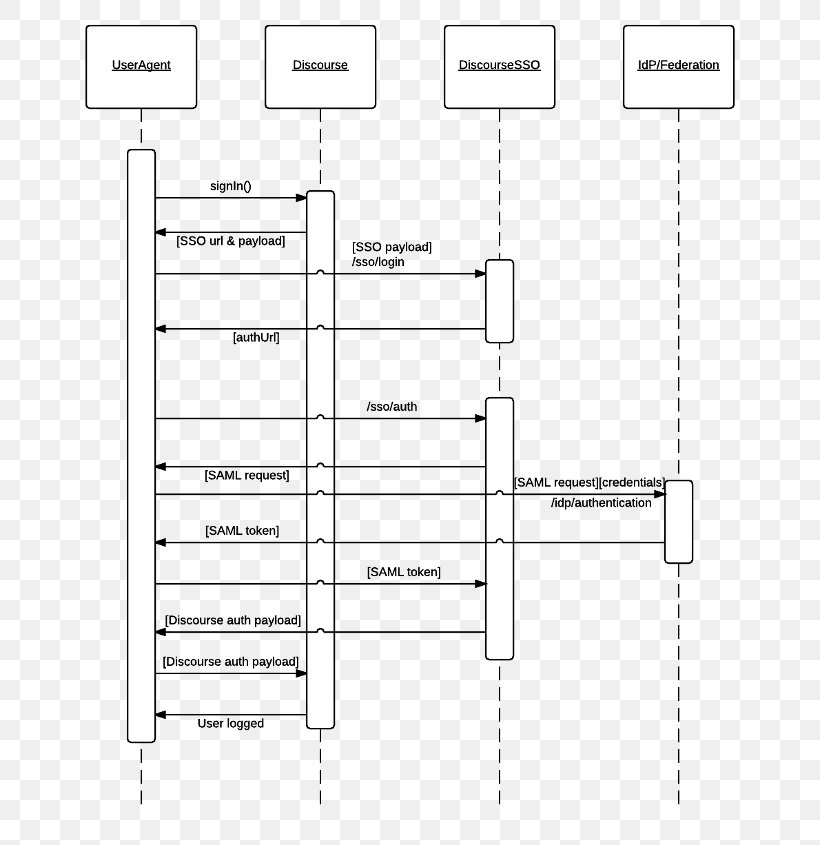
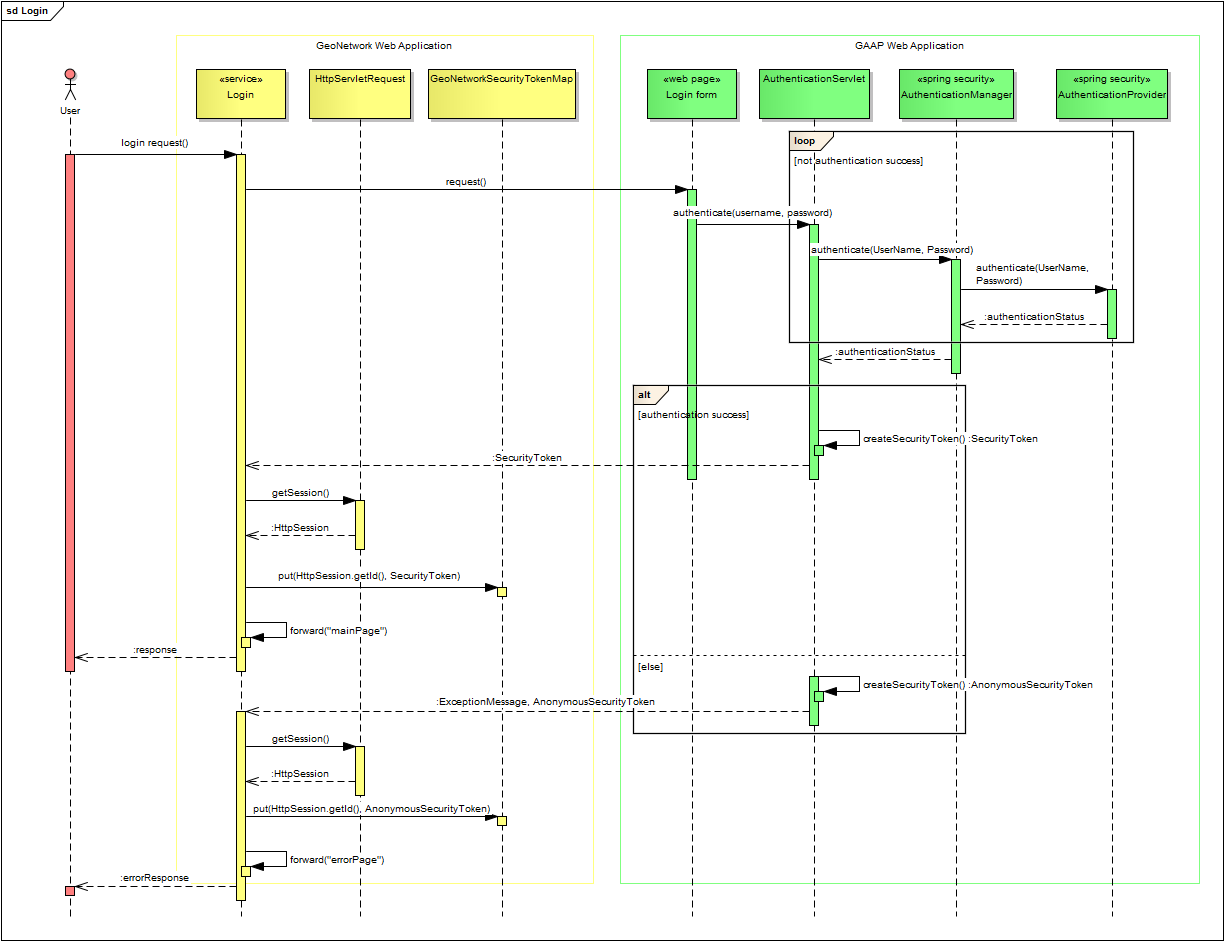
Shibboleth Sequence Diagram Security Assertion Markup Language OpenID Connect, PNG, 700x845px, Shibboleth, Area, Authentication, Black And

task #6118: evaluate spring-security-auth2 and spring-cloud-security as a framework for OAuth2 - EDIT - EDIT Project Management













![MS-NNS]: Protocol Examples | Microsoft Learn MS-NNS]: Protocol Examples | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-nns/ms-nns_files/image003.png)