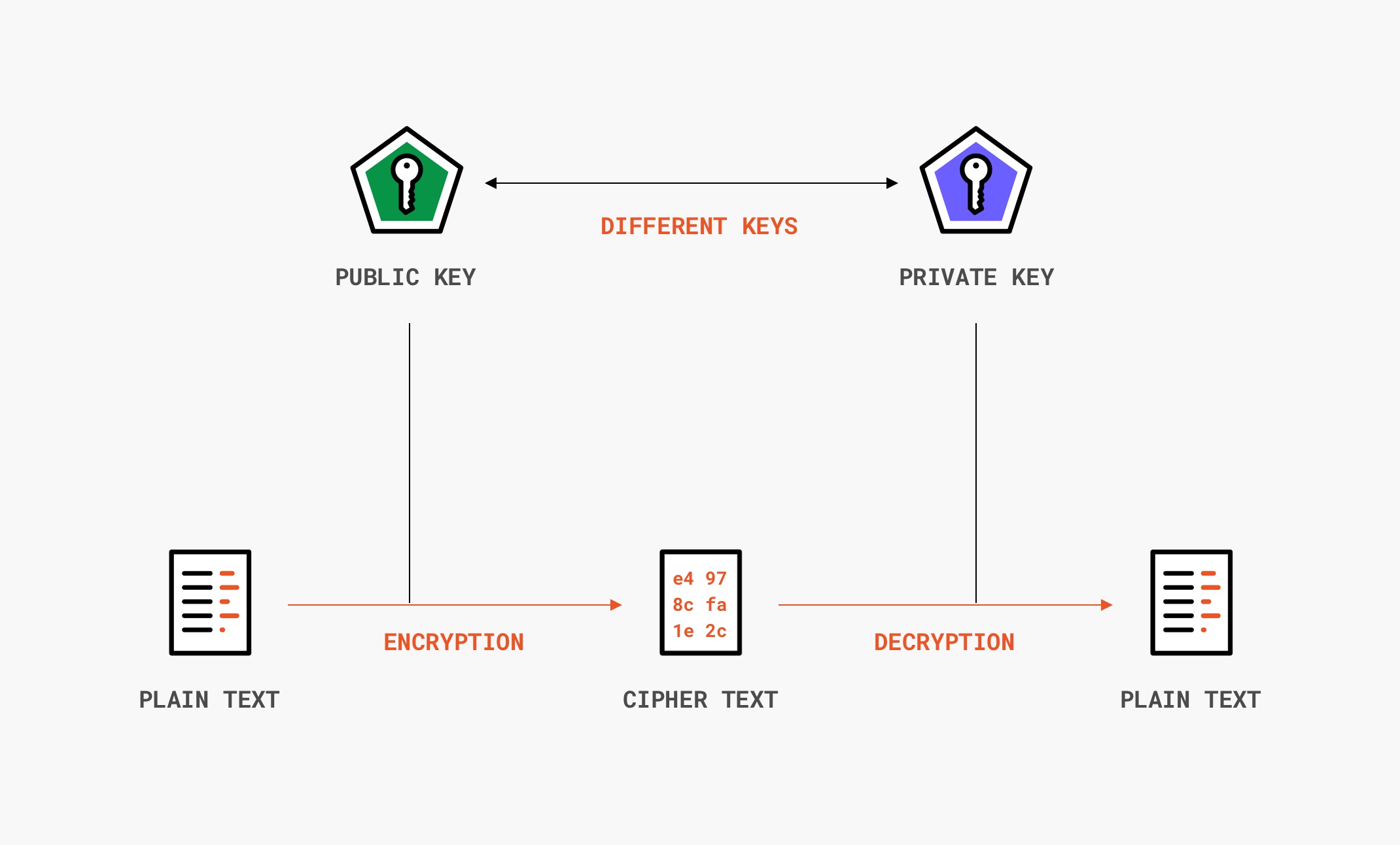
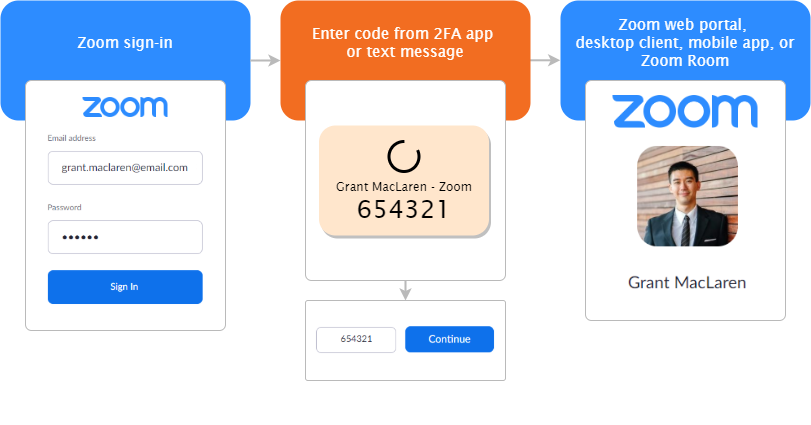
Yubikey Hardware Token | Guide to setup Yubikey Hardware Token as 2FA method for Drupal | Other TFA Methods | Drupal Wiki guide on Drupal.org
Titan Security Key: Google stellt eigenen Hardware-Sicherheitsschlüssel vor - Netzpolitik - derStandard.de › Web

Arten der Zwei-Faktor-Authentifizierung – Vor- und Nachteile: SMS, Authenticator-Apps, YubiKey | Offizieller Blog von Kaspersky