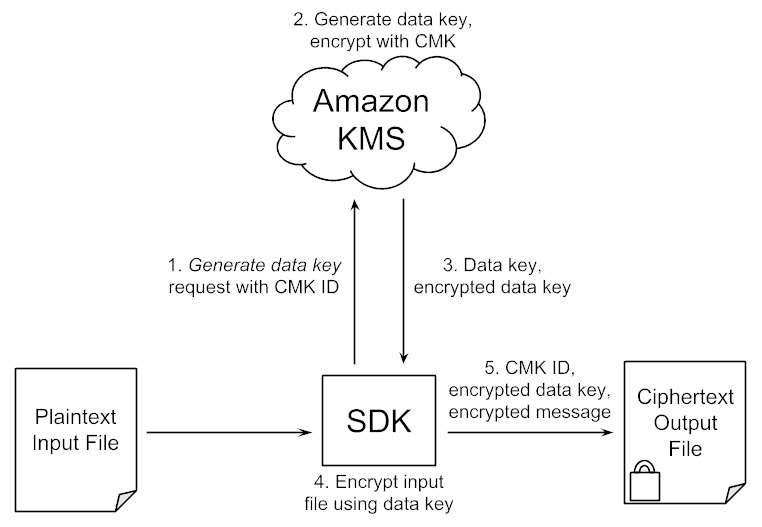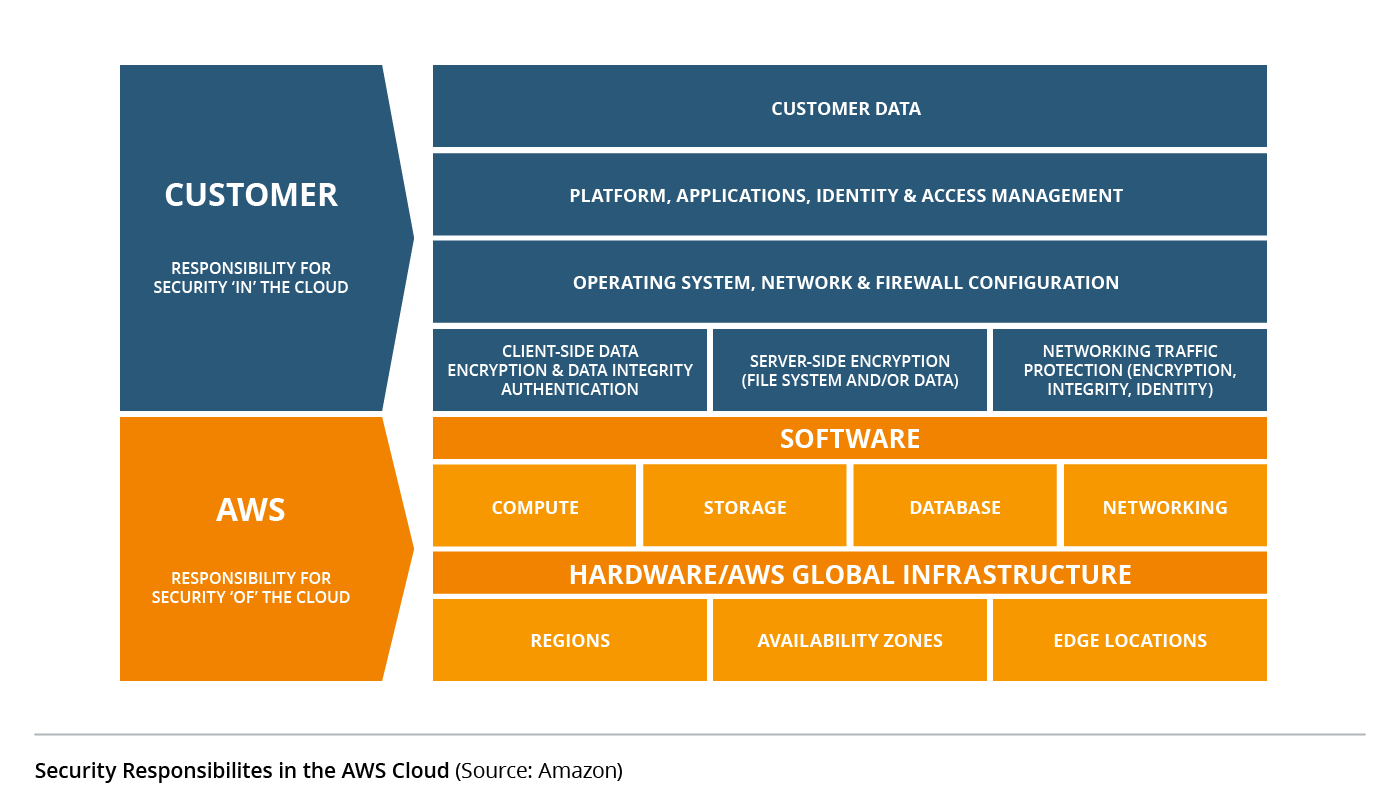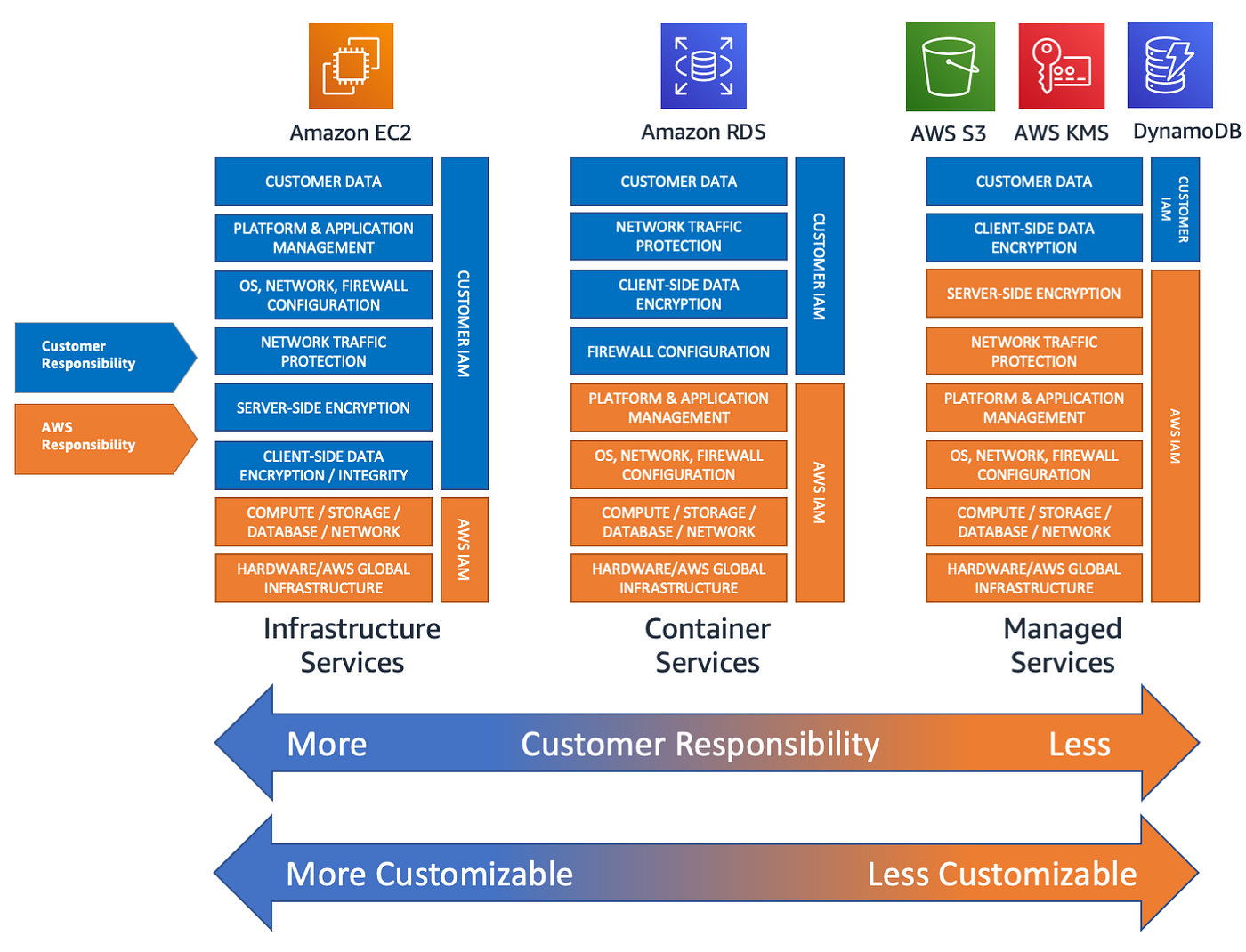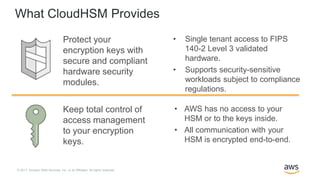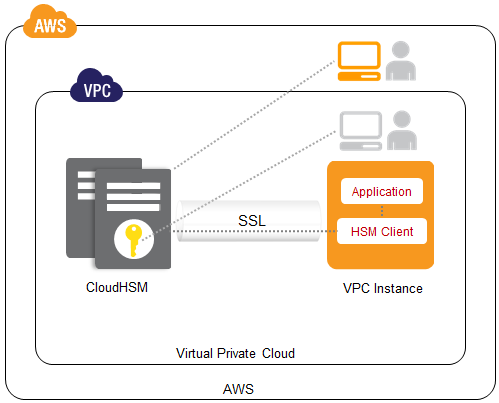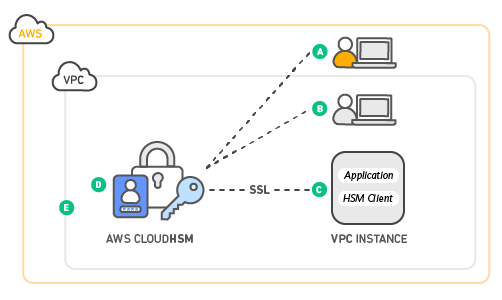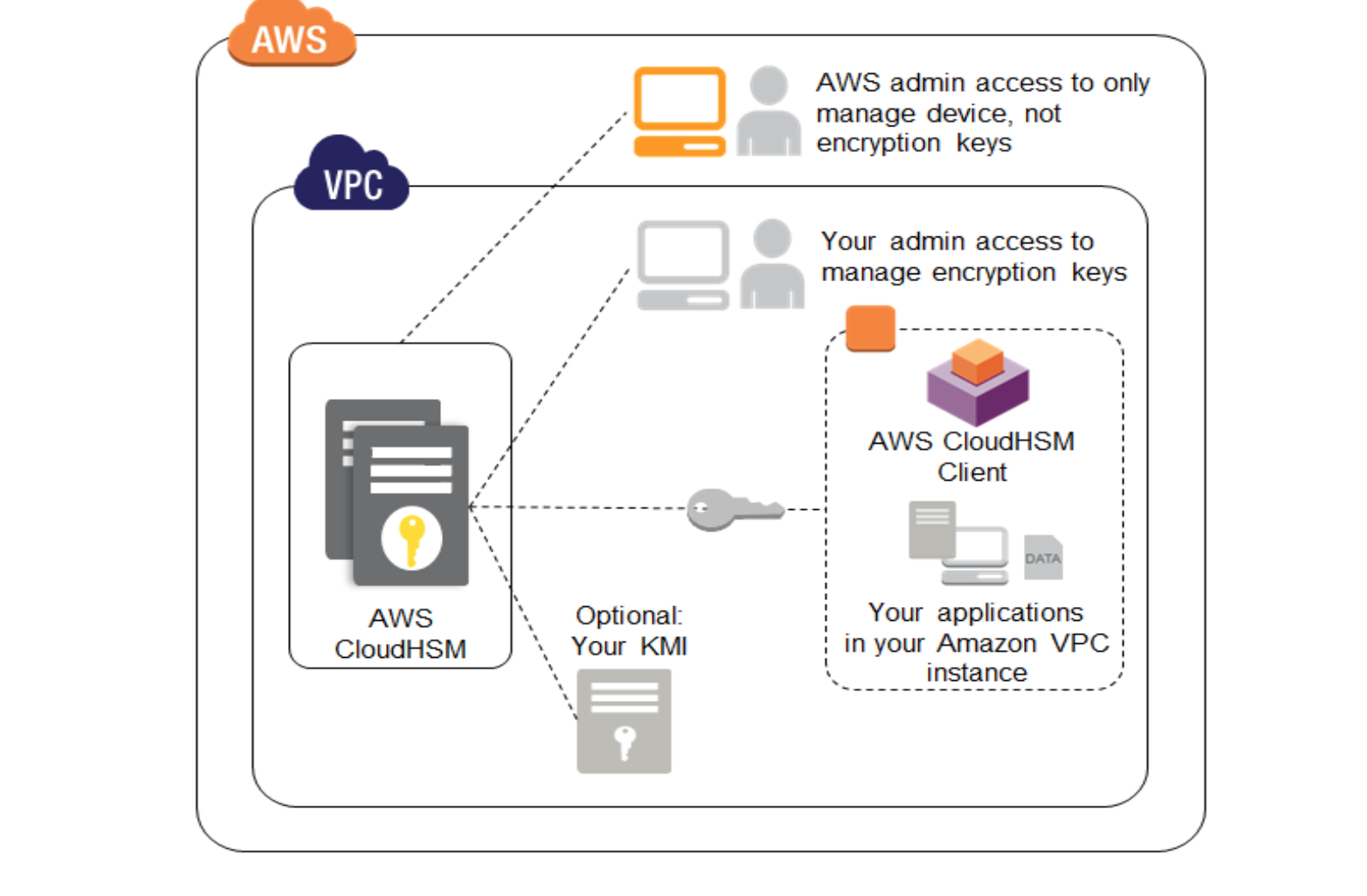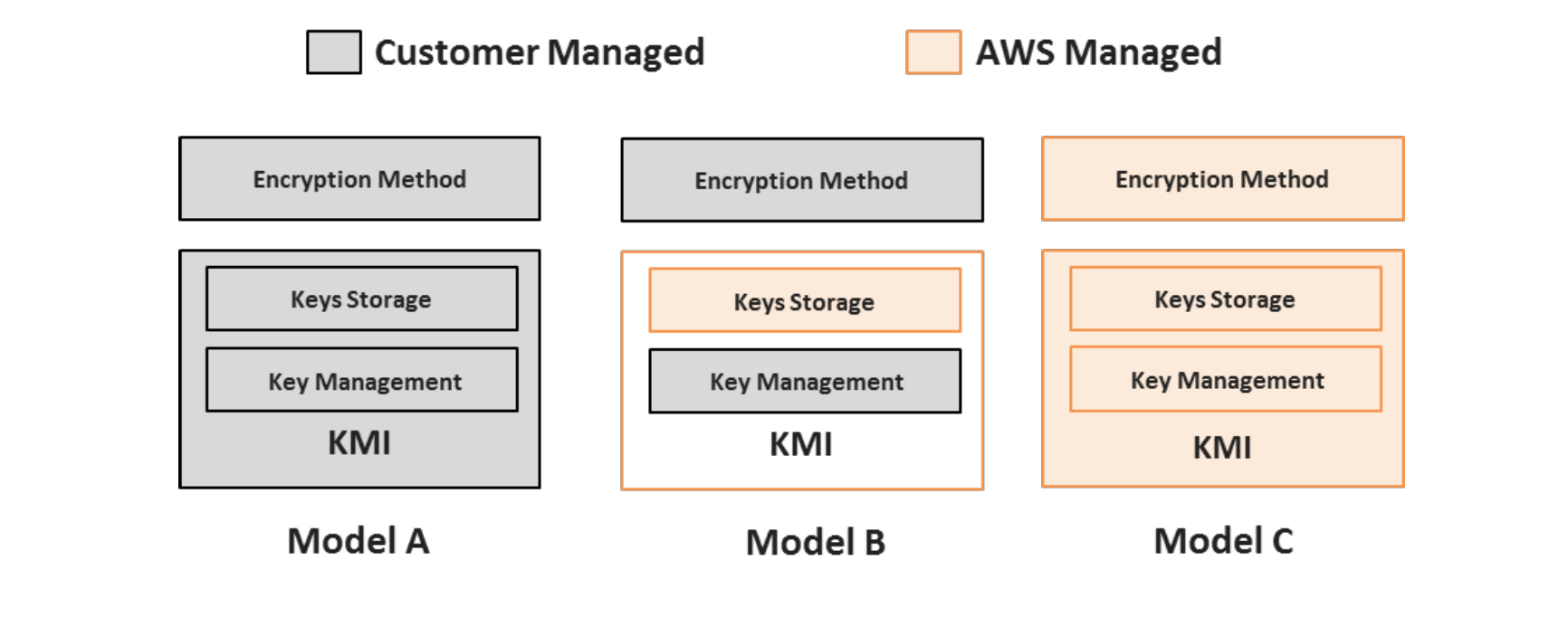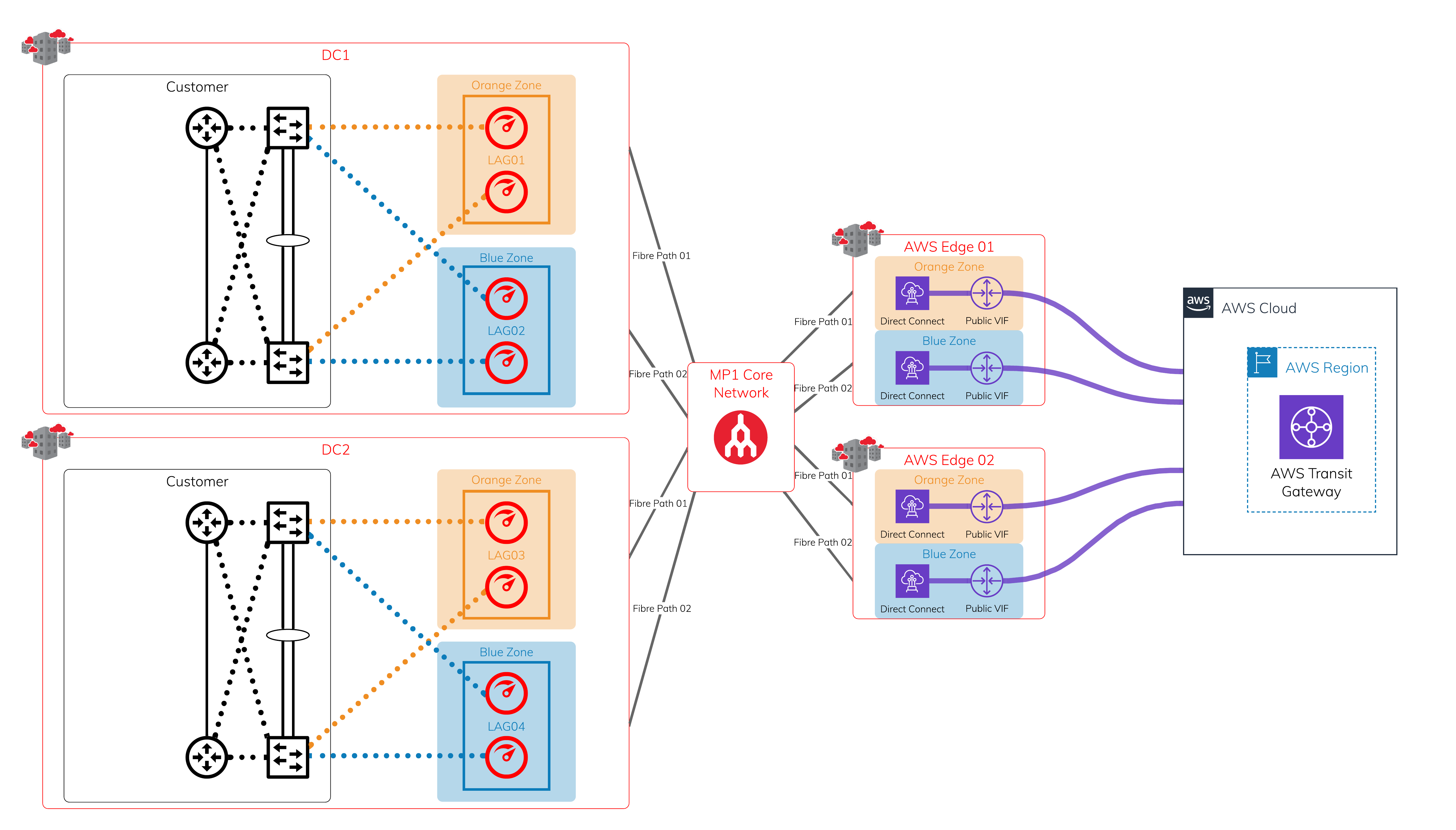
AWS Encryption Options for High Throughput and High Resilience - Megaport Documentation - Megaport Documentation
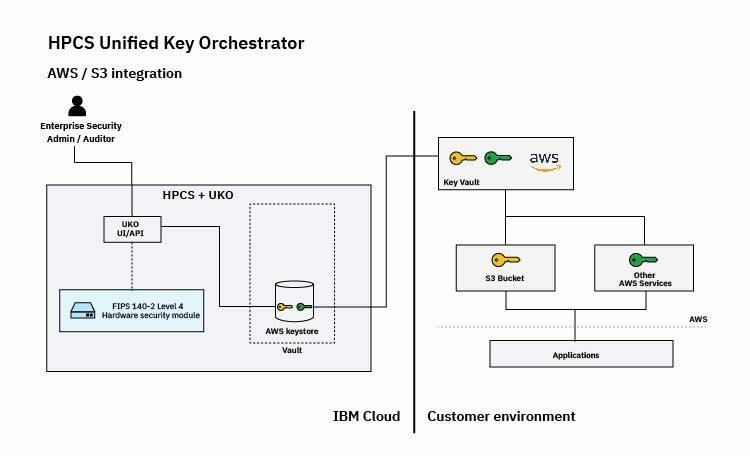
Securely manage AWS S3 encryption keys with IBM Cloud Hyper Protect Crypto Services with Unified Key Orchestrator - IBM Developer

Demystifying KMS keys operations, bring your own key (BYOK), custom key store, and ciphertext portability | AWS Security Blog
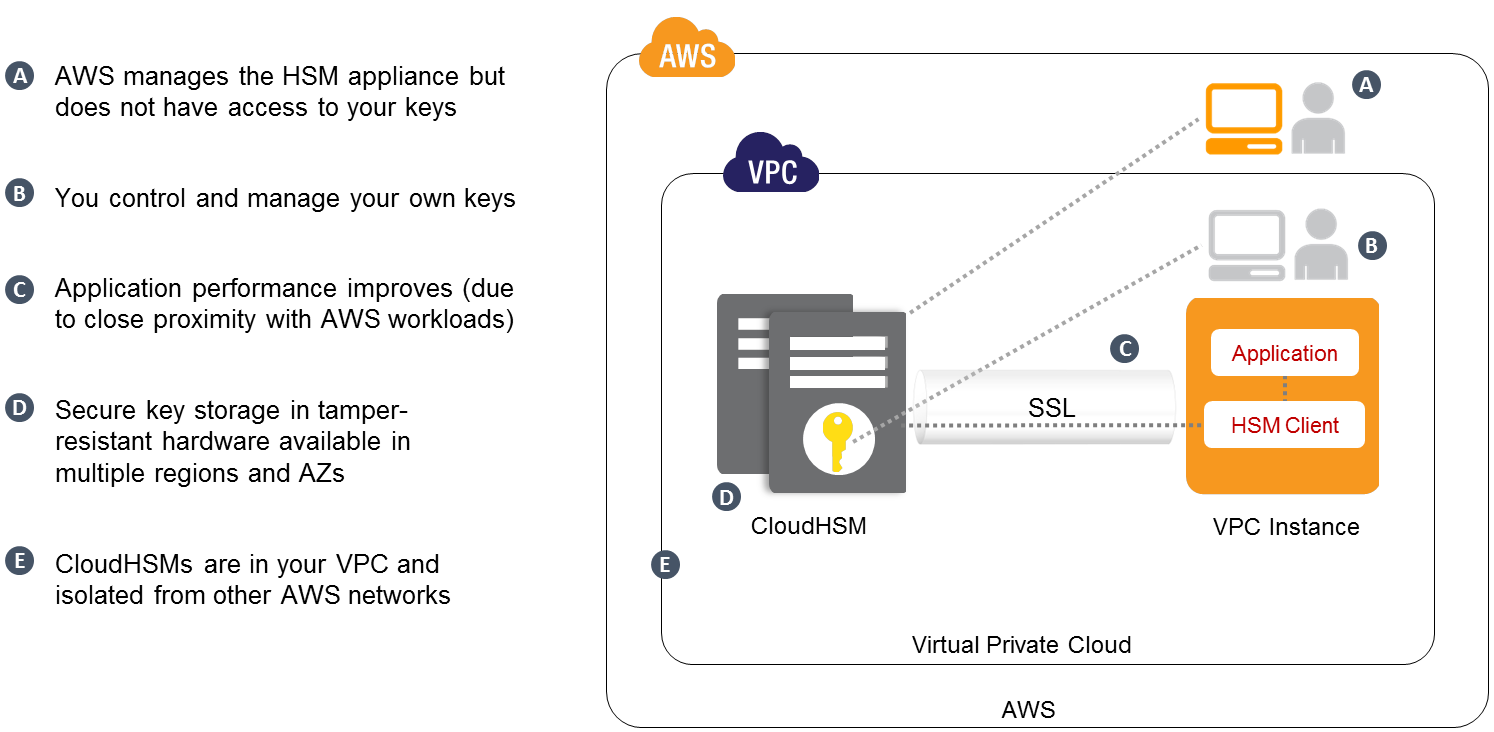
Amazon Web Services Launches CloudHSM, A Dedicated Hardware Security Appliance For Managing Cryptographic Keys | TechCrunch